In what might seem a sci-fi movie, researchers at the Usenix Security Conference have demonstrated that it is possible to hack into the human brain to extract information.
Scientists have made use of Brain-Computer Interfaces (BCI) which are popularly used in the gaming and life-sciences industries. In the past few decades, BCIs have been used in medical domains to help simulate neuro activities for patients with neuromuscular disorders. There are even cheaper BCI headsets for gamers which are less accurate versions of EEG (Electroencephalograph or Brain Electrical Activity) devices, available on the market by Emotiv and NeuroSky for $200-$300.
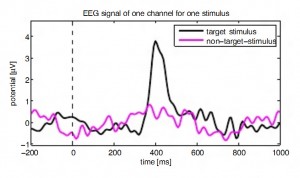
Using a P300 response, a specific brainwave pattern that the brain undergoes when it recognizes something meaningful or familiar, a face, location of your home, your DOB, your card’s PIN etc., the researchers developed a program that utilized a modified brute force attack on the brain, this was done by flashing pictures of faces, banks, PINs etc while monitoring the subject’s brain activity for a P300 response.
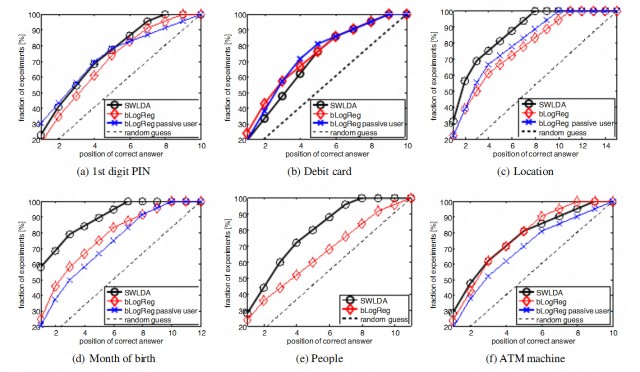
The scientists tested their program on 28 participants who obviously didn’t know that they were being subjects to a brain-hack software. In general the experiments had a 10% to 40% chance of success of obtaining useful information.
The key ingredient to capture such sensitive information from the subject is to make sure that the subject remains unaware of the fact that they are being attacked. The P300 response is triggered sub-consciously, so, making use of social engineering techniques, sensitive information can be captured.
Imagine, using a BCI device you’re playing a game designed specifically for this purpose while the hidden software in the game is extracting sensitive information from your mind using the same BCI device. This is how the scientists think of a real-life scenario.
Your darkest secrets, deepest fears would be accessible to the hackers in the near future.
Research paper: On the Feasibility of Side-Channel Attacks with Brain-Computer Interfaces
© 2012 Ajan Kancharla